What is CVE-2024-1212?
CVE-2024-1212 is a critical security vulnerability identified in Progress Kemp LoadMaster, a widely used load balancer and application delivery controller. This flaw allows unauthenticated remote attackers to execute arbitrary system commands via the LoadMaster management interface, potentially leading to full system compromise. This vulnerability affects all LoadMaster releases after 7.2.48.1 and the LoadMaster Multi-Tenant (MT) VFNs.
When Was the Vulnerability Discovered?
The vulnerability was publicly disclosed on February 21, 2024, when it was added to the National Vulnerability Database (NVD). Armis Centrix™ for Early Warning, added CVE-2024-1212 to the list of known vulnerabilities being exploited in the wild on April 8, 2024, while CISA added CVE-2024-1212 to their KEV catalog on November 18, 2024, making Armis Centrix™ for Early Warning early by 224 days.
Armis deception technology captured the exploit POC code in the threat actors staging server.
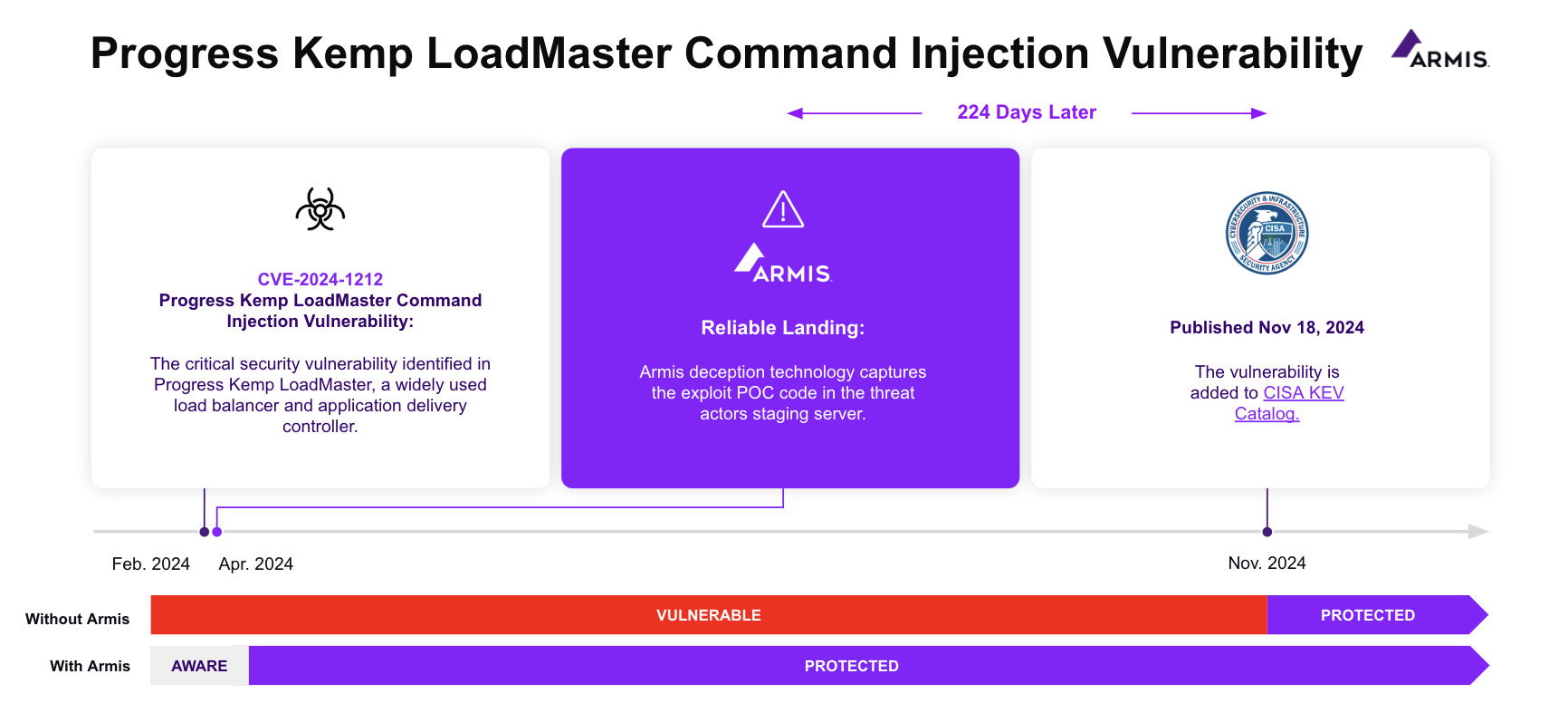
Significance of CVE-2024-1212:
Vulnerable component: the vulnerability resides in the LoadMaster management interface, which processes HTTP requests through CGI Bash scripts. A pre-auth issue in this processing flow allows for improper neutralization of special characters, leading to command injection.
Exploitation scenario: an attacker can exploit this vulnerability by sending specially crafted HTTP requests to the LoadMaster management interface. Successful exploitation requires network access to the management interface but does not require authentication, therefore making it particularly dangerous.
Impact and blast radius: exploiting this vulnerability can lead to a full system compromise. We are talking here about breach of confidentiality, integrity violation, and availability disruption (by potential denial of service attacks or system crashes). Given that LoadMaster, due to its nature, is often deployed in critical network infrastructures, the impact can be extensive, affecting multiple services and users.
Value of Timely Awareness: immediate awareness and response are crucial. Delays in addressing this vulnerability increase the risk of exploitation, which could lead to the significant operational disruptions and security breaches just mentioned above.
Mitigation and Protection:
Proactive defense and workarounds: Upgrade to version 7.2.48.10, 7.2.54.8, 7.2.59.2 or later. Progress has released patches to address this vulnerability and administrators should upgrade to the patched versions as soon as it is possible. Alternatively, if patching is not an option, systems hardening is the next available means of active defense. This includes, but is not limited to, restricting access to the LoadMaster management interface to trusted networks and administrators only and isolating management interfaces from public and untrusted networks to reduce exposure.
Continuous monitoring and updates: even after patching or hardening, it is highly recommended to monitor impacted systems for anomalous behaviours. Use intrusion detection systems (IDS) or Web application firewalls (WAF) to monitor for suspicious API activity, such as requests targeting the sensitive endpoint affected by the vulnerability. Also, regularly run vulnerability scans. By implementing these measures, organizations can mitigate the risks associated with CVE-2024-1212 and enhance their overall security posture.
Stay vigilant and ensure your systems are up-to-date to defend against evolving cybersecurity threats.
Armis Centrix™ for Early Warning is the proactive cybersecurity solution designed to empower organizations with early warning intelligence to anticipate and mitigate cyber risk effectively. By leveraging AI-driven actionable intelligence, Armis Centrix™ provides insights into the vulnerabilities that threat actors are exploiting in the wild or are about to weaponize, allowing organizations to understand their impact and take preemptive action.
Interested in learning more about Armis Centrix™ for Early Warning? Sign up for a demo today!

