What is CVE-2019-1069?
CVE-2019-1069, also known as the Task Scheduler Elevation of Privilege Vulnerability, was identified in Microsoft Windows Task Scheduler. This vulnerability allows a local attacker to escalate their privileges from a standard user to an administrator, thereby gaining full control of the affected system. This vulnerability highlights critical weaknesses in the way Task Scheduler validates certain file operations.
When Was the Vulnerability Discovered?
CVE-2019-1069 was published on June 12, 2019. The early warning technology that powers Armis Centrix™ for Early Warning has been tracking this vulnerability as exploited since March 3, 2022. Publishing a vulnerability doesn’t mean it will be exploited. To maintain safety and reduce risk, timely visibility into exploitation is key.
CISA KEV added CVE-2019-1069 to their catalog on September 18, 2024.
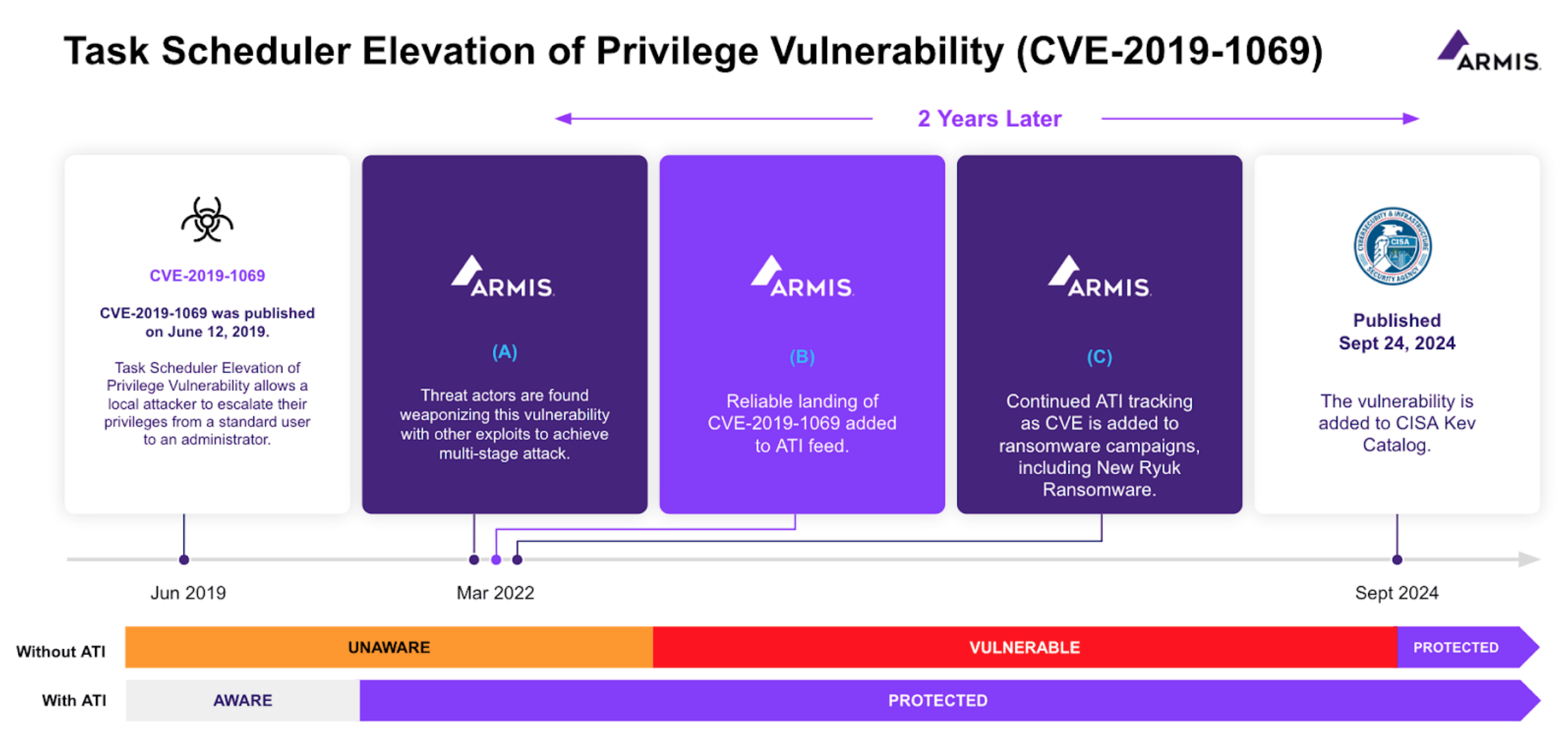
The above timeline provides an indepth look at protection against CVE-2019-1069 with and without early warning threat detection.
How Does CVE-2019-1069 Work?
The vulnerability stems from improper handling of user permissions within the Task Scheduler service. Specifically, it relates to the way the service validates file operations. An attacker exploiting this vulnerability can execute tasks with elevated privileges, leading to a complete system compromise.
Active Exploits and Threat Landscape
Since its discovery, CVE-2019-1069 has been actively exploited in the wild. It has been particularly prevalent in targeted ransomware attacks, including New Ryuk Ransomeware, where it is used in conjunction with other exploits to achieve a multi-stage attack. The vulnerability has been a favorite among both cybercriminals and state-sponsored groups, often used to gain persistence and broaden the impact of their attacks.
The Discovery by Armis Centrix™
The technology that powers Armis Centrix™ for Early Warning identified this vulnerability as exploited long before it became widely acknowledged. The proactive approach, including AI-driven intelligence that monitored dark web chatter, showcases the importance of being ahead of threat actor exploitation to prevent attacks before they impact your environment.
Impact on Enterprises
Successful exploitation of CVE-2019-1069 allows attackers to elevate their privileges from a regular user to an administrator. This elevation grants them full control over the affected system, enabling them to install programs, view or change data, or create new accounts with full user rights.
Full System Compromise
With administrator privileges, attackers can execute arbitrary code, install malware, or steal sensitive information. This not only compromises the affected system but can also serve as a foothold for lateral movement within the network, potentially leading to broader organizational breaches.
Lateral Movement and Persistence
Attackers can use the compromised system as a base to move laterally within the network, gaining access to additional systems and expanding the scope of their attack. Elevated privileges also provide attackers with the ability to install backdoors and maintain long-term access to the network, making detection and removal significantly more challenging.
Mitigation and Protection
The most effective way to mitigate the risks associated with CVE-2019-1069 is to apply the May 2019 security update from Microsoft. This patch addresses the improper permission handling in the Task Scheduler service, thereby preventing privilege escalation.
Least Privileges for All Systems
Implementing the principle of least privilege can minimize the risk of privilege escalation in the event of exploitation. Restricting local user privileges ensures that only necessary permissions are granted, reducing the potential impact of a compromised account.
Network Segmentation
Isolating critical systems through network segmentation can limit an attacker’s ability to move laterally within the network. By creating distinct segments for different parts of the organization, enterprises can contain the impact of a breach and protect sensitive data.
Conclusion
The discovery of CVE-2019-1069 as exploited by the technology that powers Armis Centrix™ for Early Warning underscores the significance of early warning threat intelligence in preemptively identifying and mitigating cybersecurity risks. By staying ahead of potential vulnerabilities and threats, organizations can better protect their systems and sensitive data from malicious actors.
For more detailed information and updates, refer to these resources:
Stay vigilant and ensure your systems are up-to-date to defend against evolving cybersecurity threats.
Armis Centrix™ for Early Warning is the proactive cybersecurity solution designed to empower organizations with early warning intelligence to anticipate and mitigate cyber threats effectively. By leveraging AI-driven actionable threat intelligence, Armis Centrix™ provides insights into potential threats, allowing organizations to understand their impact and take preemptive action.
Interested in learning more about Armis Centrix™ for Actionable Threat Intelligence? Sign up for a demo today!

