Prioritization Security Challenges
When the number of vulnerabilities and security findings are increasing exponentially, security teams struggle to identify and focus their efforts on the findings that have the highest risk to their business.
Number of Security Findings Increasing Exponentially
Faced with the adoption of new technologies straining their already overloaded processes, security teams have taken tactical approaches to dealing with a flood of security issue alerts, without enough information to prioritize and operationalize remediation for distributed operations teams.
Holistic Risk Understanding
For most organizations, prioritization is a time-consuming, manual process that often relies on technical severity scoring like CVSS in isolation from exploitability, asset priority and business impact. Most prioritization models are black box, with limited configurability for the organization’s specific risk concerns.
Which Priority is the Real Priority
Because vulnerability management teams now have responsibility for a much broader range of security issues – not just host vulnerabilities, but also cloud, code and AppSec findings – they often struggle to determine which of the priorities identified by siloed tools are the most urgent.
Armis Centrix™ for VIPR Pro – Prioritization and Remediation

Address the Vulnerabilities and Security Findings That Matter
Focus on the most critical findings for your business and environment by combining severity and exploitability with asset risk and business criticality.
Automated and adaptable risk prioritization identifies the most critical findings, and provides fix information
Armis Centrix™ for VIPR Pro – Prioritization and Remediation automates sifting through the noise to focus on the most critical findings across security domains that pose the highest risk to the organization. Combine real-world threat intelligence to contextualize finding severity, correlated information for asset profiles, attributes and properties, as well finding exploitability in your own business environment.
For assets ingested from the Armis Centrix™ platform, asset criticality is automatically defined based on insights derived by the AI-driven Asset Intelligence Engine, but can also be customized to meet the organization’s own definition. This combination of unique asset context and risk analysis enables the users to identify the findings and provide the fix for reducing risk for their organization.
Focus on High-impact Fixes
By connecting findings to cloud assets and services, and understanding the infrastructure used to deploy and provision these assets in the context of an application, Armis is able to pinpoint the root cause for related run-time or production security findings – and identify which fix will resolve multiple findings.
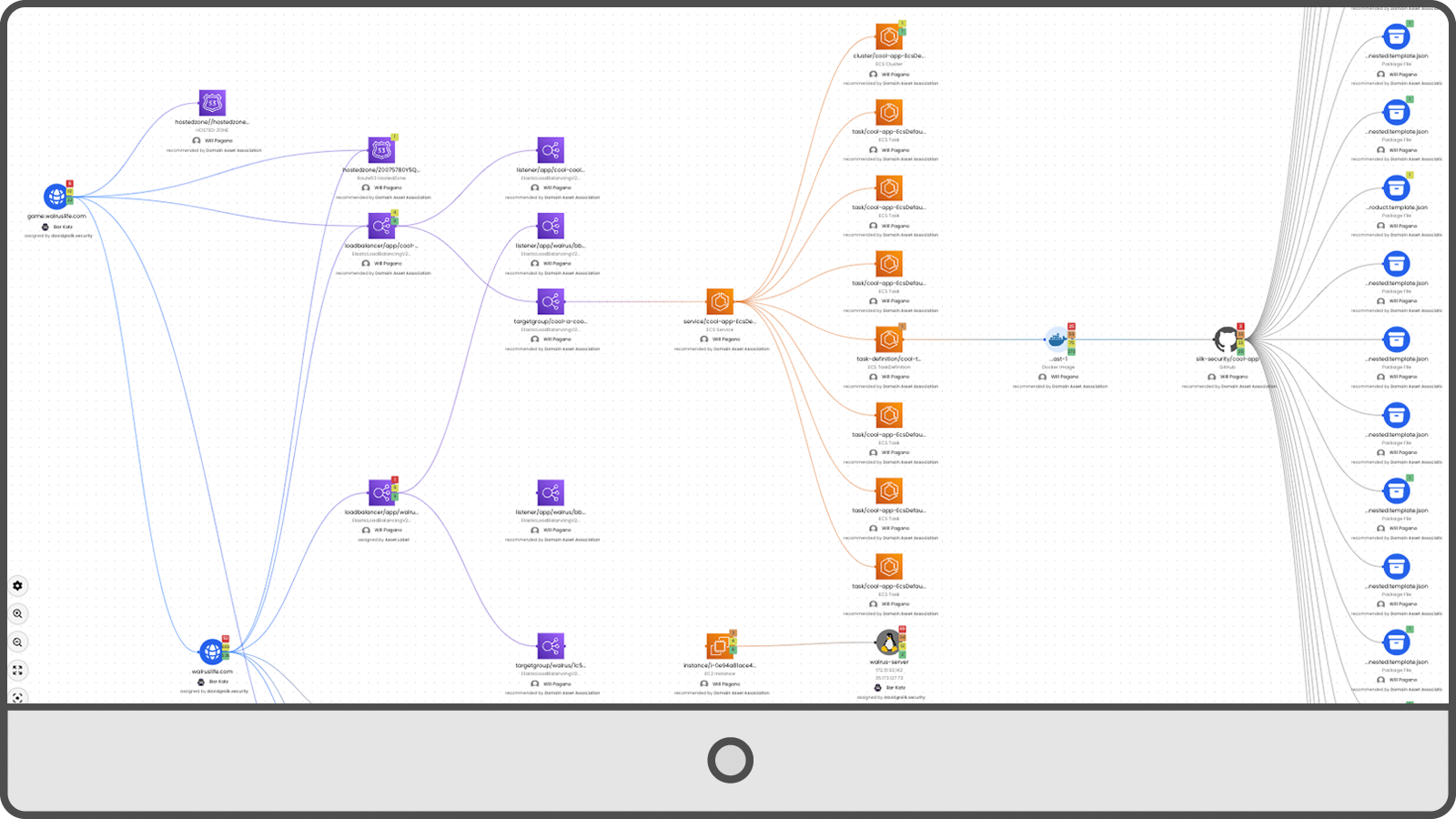
Closing the Loop: Making Security Everyone’s Business with Prioritization & Collaboration
"Armis Centrix™ for VIPR Pro – Prioritization and Remediation has positively impacted both the productivity and the efficiency of the security team in identifying risks to the business, as well as how the function of security is integrated into our development processes. The security team can collaborate more closely with development teams responsible for the fix implementation of identified priorities, and improve our overall risk profile."
Frank Baalbergen
CISO, Mendix
Additional Resources
White Paper: Modernizing Vulnerability Management to Reduce Risk
This white paper discusses the problems with traditional vulnerability management processes and how to modernize them.
Solution Brief: Armis Centrix™ for VIPR Pro – Prioritization and Remediation
Modern organizations are grappling with a barrage of security alerts and scaling the prioritization and remediation process to secure the attack surface. Armis Centrix™, addresses the gap in cybersecurity between security findings and actionable remediation.
The Invisible Front Line: AI-powered Cyber Threats Illuminate the Dark Side
Immerse yourself in the 2024 Armis Cyberwarfare Report to uncover how organizations and governments worldwide are confronting escalating threat levels head-on. Secure your copy of the report now and unlock invaluable insights into this pressing global challenge.

