What is CVE-2021-41277?
CVE-2021-41277 is a Local File Inclusion (LFI) vulnerability discovered in the GeoJSON API of Metabase, a widely used open-source business intelligence and analytics platform. This flaw arises due to insufficient input validation when handling file paths in API requests. By exploiting this weakness, an attacker can access arbitrary files from the underlying server’s file system, potentially exposing sensitive data such as configuration files, credentials, and environment variables. The vulnerability affects versions of Metabase prior to 0.40.5 and 1.40.5.
When Was the Vulnerability Discovered?
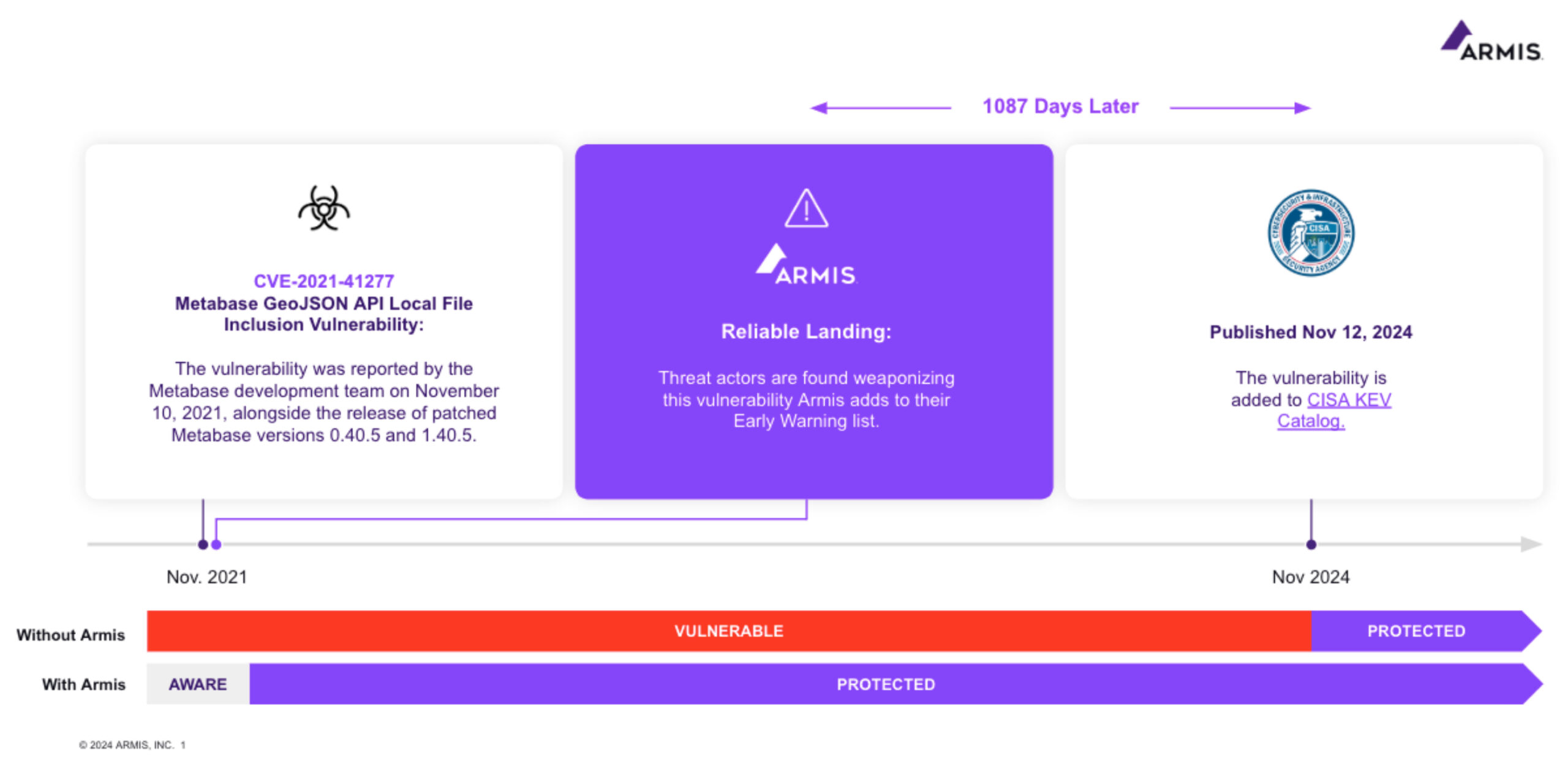
The vulnerability was reported by the Metabase development team on November 10, 2021, alongside the release of patched Metabase versions 0.40.5 and 1.40.5, providing detailed information to guide users on remediation. The disclosure highlighted the critical nature of the issue and underscored the importance of prompt action for affected users.
Armis Centrix™ for Early Warning, added CVE-2021-41277 to the list of known vulnerabilities being exploited in the wild on November 21, 2021, based on intelligence from November 17, 2021.
CISA added CVE-2021-41277 to their KEV catalog on November 12, 2024, making Armis Centrix™ for Early Warning early by 1087 days.
The Discovery by Armis Centrix™
The technology that powers Armis Centrix™ for Early Warning identified this vulnerability as exploited before it became widely acknowledged. The proactive approach, including AI-driven intelligence that employed smart honeypots and monitored dark web chatter, showcases the importance of being ahead of threat actor exploitation to prevent attacks before they impact your environment.
Significance of CVE-2021-41277:
Vulnerable component: the vulnerability is located in the GeoJSON API endpoint, a feature designed to load and process geographic data in JSON format. The flaw occurs because this API does not properly sanitize or validate user-provided file paths, allowing attackers to manipulate requests and gain unauthorized access to server files.
Exploitation scenario: to exploit this vulnerability, an attacker needs direct access to the GeoJSON API endpoint. The exploitation typically involves sending a maliciously crafted API request containing a path to a local file, then the server processes the request and includes the specified file in the response without verifying its validity and, lastly, the attacker receives the file’s contents, enabling them to extract sensitive information like usernames, hashed passwords, API keys, or database credentials. This attack, in some configurations, does not require authentication, making it particularly dangerous for publicly accessible Metabase instances.
Impact and blast radius: direct impact from exploitation includes exposure of sensitive server-side data, such as application configuration files, database connection strings, environment variables (e.g., AWS keys, API secrets), user credential files and more. Initial blast radius for this vulnerability includes any Metabase server running versions prior to 0.40.5 or 1.40.0, but the risk extends to integrated systems and databases, as attackers could use stolen credentials to pivot further into the environment.
Value of Timely Awareness: understanding this vulnerability is critical for security teams to prevent potentially devastating breaches because, if exploited, LFIs could act as a stepping stone for more sophisticated attacks, including privilege escalation through stolen credentials and lateral movement within the network by exploiting compromised systems. Timely detection and patching prevents attackers from exploiting this vulnerability in the wild.
Mitigation and Protection:
Proactive defense and workarounds: at both the time of initial disclosure, as well as today, upgrading Metabase to the latest secure versions (0.40.5 or 1.40.5) is the preferred way to achieve protection. Alternatively, if patching is not an option, systems hardening is the next available means of active defense. This includes: disabling unused features (i.e. if GeoJSON API functionality is not required, disable it to reduce the attack surface), restricting API access (i.e. configure firewalls or reverse proxies to block access to the GeoJSON API from untrusted sources, or Ideally, restrict API access to internal networks or specific IP addresses), set restrictive permissions on sensitive files (ensuring that only the necessary processes can access them, or using application whitelisting to control which directories the API can access).
Continuous monitoring and updates: even after patching or hardening, it is highly recommended to monitor impacted systems for anomalous behaviours. Use intrusion detection systems (IDS) or Web application firewalls (WAF) to monitor for suspicious API activity, such as requests targeting sensitive file paths. Regularly run vulnerability scans against any Metabase server in the environment to identify and address potential misconfigurations or newer, unpatched vulnerabilities. Finally, audit API logs, by analyzing API usage logs to detect repeated file access attempts or other signs of exploitation attempts.
Stay vigilant and ensure your systems are up-to-date to defend against evolving cybersecurity threats.
Armis Centrix™ for Early Warning is the proactive cybersecurity solution designed to empower organizations with early warning intelligence to anticipate and mitigate cyber risk effectively. By leveraging AI-driven actionable intelligence, Armis Centrix™ provides insights into the vulnerabilities that threat actors are exploiting in the wild or are about to weaponize, allowing organizations to understand their impact and take preemptive action.
Interested in learning more about Armis Centrix™ for Early Warning? Sign up for a demo today!

